In today’s digital age, the importance of cybersecurity cannot be overstated. As we use more online services, it’s super important to keep our personal info safe from sneaky cyber threats. One big danger is something called a credential stuffing attack. These attacks are like stealthy ninjas of the internet, causing chaos for people who aren’t prepared. In this blog, we’re going to dive deep into how these attacks work, figure out their tricks, and most importantly, learn how to stop them from messing with our stuff.
What is a Credential Stuffing Attack?
To understand credential stuffing attacks, let’s first break down the term:
- Credential: Refers to the username-password combination used to access an online account.
- Stuffing: The act of using automated tools to repeatedly input these credentials into various websites or services.
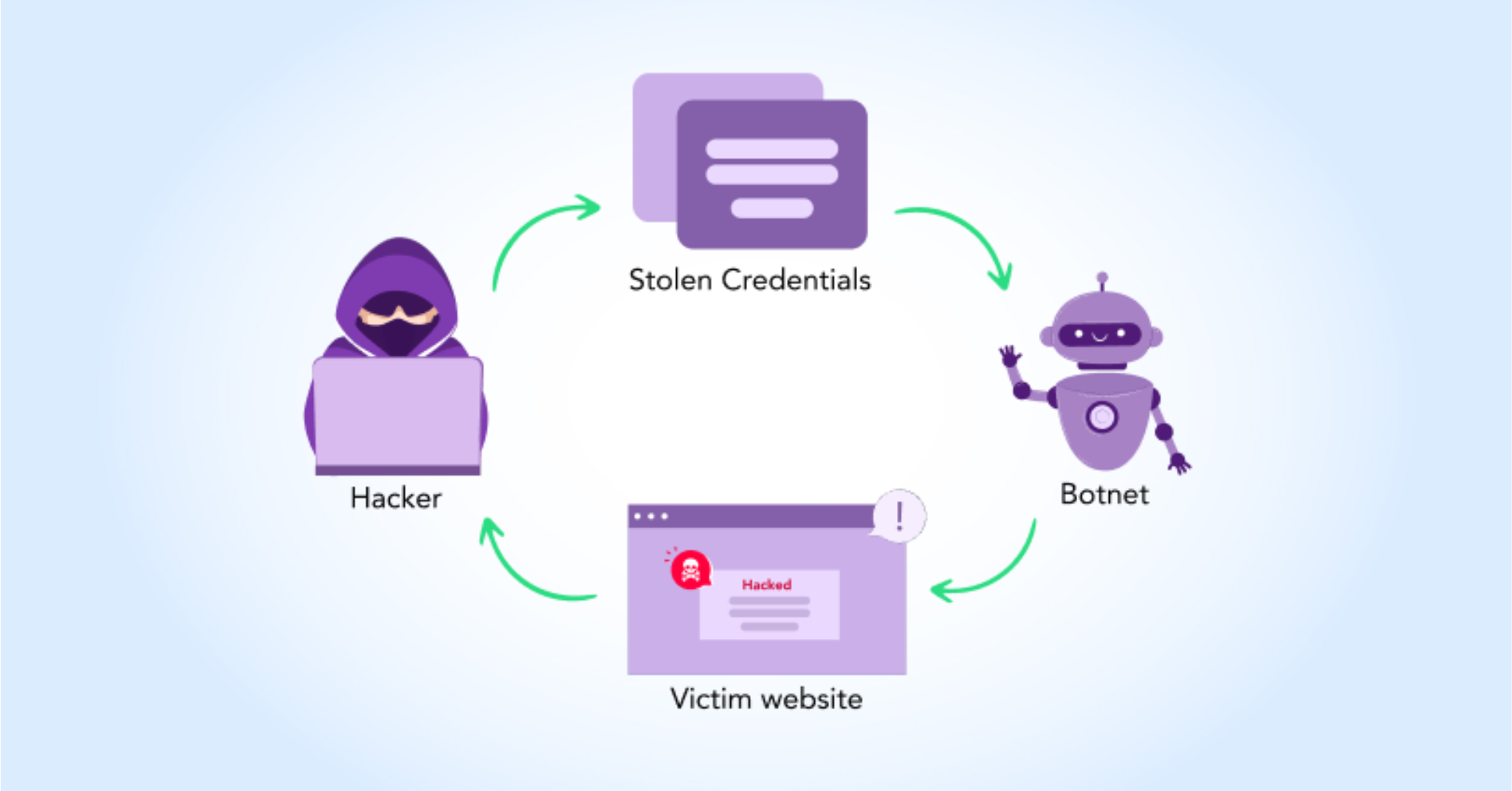
Now, let’s put them together: A credential stuffing attack is a type of cyberattack where cybercriminals use automated tools to input large sets of stolen usernames and passwords (usually acquired from data breaches) into various websites or online services, with the aim of gaining unauthorised access to user accounts.
How Does a Credential Stuffing Attack Work?
- Data Breaches: Cybercriminals often obtain large databases of usernames and passwords through data breaches of websites or services.
- Automated Tools: Using automated tools like bots or scripts, attackers systematically try these stolen credentials on other websites or services. These tools can rapidly try thousands or even millions of combinations in a short period.
- Account Access: If a username-password combination matches an existing account on the targeted website or service, the attacker gains unauthorised access to that account.
How to Stay Safe from Credential Stuffing Attacks:
Given the potential risks associated with credential stuffing attacks, it’s crucial to take proactive steps to protect yourself:
Use Unique Passwords: Avoid using the same password across multiple accounts. Instead, use complex and unique passwords for each account. Consider using a password manager to generate and store strong passwords securely.
Enable Two-Factor Authentication (2FA): Implementing 2FA adds an extra layer of security to your accounts. Even if your password is compromised, attackers would still need another form of authentication to gain access.
Monitor Your Accounts: Regularly monitor your online accounts for any suspicious activity. If you notice any unauthorised access or unusual behavior, take immediate action to secure your account and change your password.
Stay Informed about Data Breaches: Keep yourself informed about data breaches and security incidents. Websites like Have I Been Pwned allow you to check if your email address has been involved in any known data breaches.
Educate Yourself: Stay informed about cybersecurity best practices and common attack techniques like credential stuffing. Understanding these threats can help you recognise potential risks and take appropriate measures to mitigate them.
Limit Login Attempts: Websites and online services should implement rate limiting and account lockout mechanisms to prevent automated credential stuffing attacks. This can help deter attackers by making it more difficult to guess or brute force login credentials.
In conclusion, credential stuffing attacks pose a significant threat to the security of online accounts. By understanding how these attacks work and taking proactive steps to protect yourself, such as using unique passwords, enabling 2FA, and staying informed about data breaches, you can significantly reduce the risk of falling victim to such attacks. Remember, safeguarding your online identity is essential in today’s digital world, and staying vigilant is key to staying safe.