As email continues to be the primary form of communication for business, the number of email-based attacks have increased. In fact, 94% of malware is spread through emails, hosted behind documents, or URLs that lead to malicious websites. Once a malware enters into a system, it can have a devastating impact to a business. Knowing these risks and the threats that lurk in mailboxes is the first step towards building a defence. That’s why we’ve created a list of the top email threats you need to be aware of to protect your business.
1. Phishing
Phishing has become one of the most pervasive cyber threats today, with malicious actors seeking to exploit unsuspecting victims via fake emails or social media messages. These crafty correspondences contain links that often direct users to carefully constructed phishing sites in an effort to capture personal or business information, or deploy the malware into these systems to extract that information.
| The number of unique phishing sites detected worldwide | 611,877 |
| Online Industry most targeted by a Phishing attack | Financial Institutions |
| The country most targeted by Phishing attacks | Brazil |
| Share of employees who click on malicious email links | 2.94% |
| The age group most likely to click on a Phishing email | 31 to 40 Years |
| Share of 16 to 24 years old who made security mistakes that their company will never know about | 42% |
| Most common delivery method causing ransomware infections | Spam/ Phishing emails |
| Share of phishing sites using .com as top-level domain | 32% |
| Share of Phishing sites using a brand name in the domain name | 29% |
Source:- https://www.statista.com/
Types of Phishing attacks
- URL Phishing: This is one of the most common types of threats. URL phishing involves cybercriminals sending out malicious links or attachments in an effort to gain access to personal information or passwords. The link or attachment will usually direct you to a webpage that looks legitimate but is actually designed to steal your data or download malicious software onto your device. It’s important to remember that these pages can look incredibly convincing; they may even be nearly identical copies of real websites!
- Spear Phishing is a more targeted form of phishing attack that specifically targets an individual (or group) with carefully crafted emails designed to appear as though they have been sent from someone they know and trust. This type of attack typically involves scammers sending emails with malicious links or attachments in an attempt to gain access to personal information such as credit card numbers or banking credentials.
- Lateral Phishing is a type of attack that involves sending emails from within a company in order to gain access to sensitive data. These attacks target specific departments within organizations, such as HR or finance, by spoofing internal emails from trusted staff members in order to convince victims into providing confidential information. As with other forms of phishing, lateral attacks can also involve malicious links and attachments intended to steal data or install malware on a victim’s device.
2. Spam
Spam is any kind of digital communication that gets sent out in bulk without the consent of the recipients. Spam emails are an increasingly prevalent way for malicious actors to deceive unsuspecting victims. Many spam messages contain links with Trojan horses, phishing schemes and other harmful content that can be detrimental. These activities tend to infect networks or devices with viruses or worms, which are often sent out as bulk email messages in order to gain access to sensitive data such as social security numbers or bank account details.
3. Business Email Compromise (BEC)
Business Email Compromise typically referred to as BEC, is an insidious form of attack that takes advantage of unsuspecting individuals by leveraging the credibility and trust gained from spoofed or impersonated corporate email accounts. Highlighting this point are a few noteworthy examples including one Latvian cybercrime gang that scammed Facebook and Google out of over $121 million between 2013-2015 using fake invoices sent via email; DHL’s 2018 incident where attackers targeted employees with malicious attachments disguised in job postings; plus Netflix’s recent encounter when hackers were able to generate false orders for customers due primarily to lack of two-factor authentication security measures.
4. CEO fraud
In a harrowing attack, CEO fraud sees malicious actors take on the persona of a company executive, such as the CEO with the goal of tricking an unsuspecting staff member into carrying out actions that lead to leaking business information or making financial transactions.
CEO fraud is an email scam that preys on people’s stress to manipulate them into sending money. In this case, the attacker impersonates a real executive by using a similar but fake address and applies pressure on their recipient. Perhaps most alarmingly, they attempt wire transfer fraud, one of the more common tactics used in such scams.
Here’s an example of a CEO fraud attack:
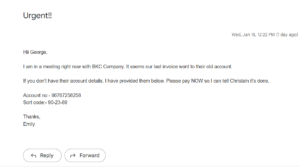
5. Malware
Email remains one of the most popular delivery mechanisms for malicious software, with 94 per cent of all malware infiltrating its way through inboxes. Amongst this widespread threat, ransomware is particularly prevalent; attackers use it to lock email communications as well as other critical documents and files until a ransom demand has been met. To wreak havoc, cybercriminals embed viruses or scripts in documents which trigger additional downloads from external sites when opened. Three common types of attack include volumetric malware that targets networks with large amounts of data-traffic, zero-day threats where an individual system’s vulnerability can be exploited before any patching action can take place and URL attacks leveraging compromised URLs sent via emails to obtain user login credentials amongst others.
6. Data Exfiltration
Data exfiltration is the unauthorized removal of data from a device. The global market for Data Exfiltration is estimated to reach USD 77920 million by 2028 due to complications arising from the ongoing COVID-19 pandemic and Russia-Ukraine War Influence. This growth, at a CAGR of 6.6%, will be driven primarily by malicious attacks against networks or machines seeking access to confidential data as well as accidental losses that result from human error. Definitive prevention protocols must therefore be implemented in order to protect businesses and organizations worldwide both now and into the future.
7. Scam
Email scamming is a serious threat to individuals worldwide, with cybercriminals leveraging fraudulent schemes to steal personal information and money. Common examples of these scams include fake job postings, lottery prizes, inheritance notifications and investment opportunities. According to the latest data from 2022 – nearly two-thirds (39%)of all spear-phishing attacks target people through scam emails; in fact, this was reported as the second most common crime globally last year! Furthermore, it’s estimated that $55 billion were lost around the world due to scammers’ activities – representing an eye-watering 15.7% increase on 2021 figures unfortunately many victims have fallen for email scams unknowingly parting in sensitive info or making payments unnecessarily.
8. Domain Impersonation
Cybercriminals leverage domain impersonation to launch sophisticated conversation-hijacking attacks. Through subtle letter replacements or the addition of hard-to-notice characters, attackers create deceptive domains that are often difficult for victims to differentiate from legitimate ones. Taobao is a prime example; it ranks among the most commonly targeted e-commerce websites on an international scale. As of November 2022, almost 5,000 domains online used a similar spelling as Taobao’s to simulate the website, appear legitimate, and harvest personal data from unknowing users. The action of impersonating a web page’s address or URL is also known as domain spoofing. These scams can go undetected and result in serious implications – making this form of attack particularly dangerous and high impact when successful.
9. Brand Impersonation
This is malicious activity where an attacker attempts to convince victims that they are associated with reputable organizations or services. By masquerading as trusted companies or business applications, criminals can harvest sensitive information and carry out account takeovers with little effort. Common methods include service and brand hijacking, which involve the use of sophisticated techniques such as email messages spoofed from legitimate domains in order to steal credentials and uncover sensitive information. These attacks have become increasingly widespread due to their deceptive nature and should be guarded against by businesses at all levels.
10. Extortion
As data breaches become increasingly common, cybercriminals are taking advantage of stolen usernames and passwords to conduct sophisticated extortion scams.There are many forms of extortion, such as Sextortion. Sextortion attacks involve using intimate or personal information against victims in an attempt to lure money out of them. Sextortion attacks pose a particularly prevalent threat as they use intimate or embarrassing information against victims in attempts to lure money out of unsuspecting individuals. With 7 per cent of spear-phishing attacks now involving extortion schemes, employees must remain vigilant not only when it comes to business email compromise but also these types of nefarious threats.
The Titanium State of Data Exfiltration & Extortion Report for 2022 reveals that traditional security measures have been inadequate in preventing ransomware and extortion. 70% of organizations surveyed had experienced an attack within the past 5 years, with 68% reporting data exfiltration followed by 60% experiencing a subsequent extortion demand. In response to this growing threat landscape, 99 per cent of study participants are eager for improved solutions – emphasizing the urgent need for more effective ways to combat these destructive cybercriminal activities.
Email threats can present a serious risk to businesses alike if they’re not taken seriously. So it’s important to always stay vigilant when it comes to protecting yourself against these types of attacks – especially when opening attachments from unknown sources! By being aware of the potential risks posed by these malicious emails, you can help ensure the safety of your data and keep yourself secure online.
