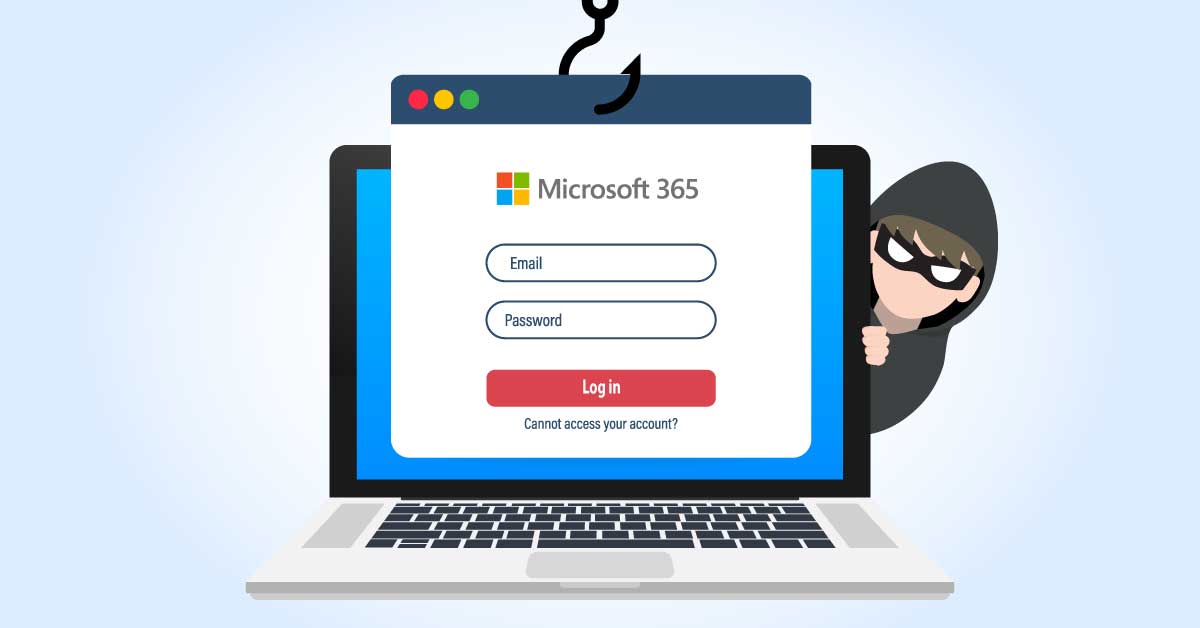
Microsoft has just discovered a new phishing attack that bypasses their Microsoft Exchange basic authentication protocols. This new phishing campaign touts a file that the recipient must read pointing to a malicious link that takes victims to a lookalike Office 365 login page. Once the victim offers up their credentials a “file not found” message is displayed.
Phishing is a type of social engineering attack often used to steal user data, including login credentials and credit card numbers. It occurs when an attacker, masquerading as a trusted entity, dupes a victim into opening an email, instant message, or text message. The recipient is then tricked into clicking a malicious link, which can lead to the installation of malware, freezing of the system as part of a ransomware attack or revealing of sensitive information.
What is a BEC attack?
BEC (Business Email Compromise) is a phishing technique in which financially motivated cybercriminals trick unsuspecting executives and employees into making payments or sending sensitive data to fraudulent accounts. Attackers accomplish this by using a variety of techniques that manipulate users into sending money or data.
Business Email Compromise attacks are notoriously difficult to prevent. Rather than use malware, cybercriminals rely on social engineering techniques and impersonation to trick people into acting on the attacker’s behalf.
Recent statistics from the FBI’s 2020 Internet Crime Report highlighted that there had been nearly 20,000 complaints of Business Email Compromise. In 2020, $1.86billion was the amount lost due to BEC attacks. Looking at the sophistication behind these attacks, it is clear that traditional threat detection solutions that analyse email headers, links and meta data is not enough to combat these attacks.
Types of Phishing attacks
Over the years, Cybercriminals have introduced new tactics to trick people into revealing sensitive information. They have examined people’s behaviour and reliance on certain communication and data storage methods. Here are a couple of examples of how cybercriminals have tricked individuals into revealing sensitive information.
Tax Season Messages
During tax season, scammers send messages regarding tax issues. A common tactic used is providing a fake link for accessing your W-2s or other tax forms. However, by sending your tax form to a fraudster, you give them all the information they need to steal your identity.
Google doc/ Dropbox/ file-sharing notifications
There may have been instances where you’ve received a subject line “someone (name) has shared a Google Doc with you.” Within the body of the message is a fake link to the document or file. However, the link doesn’t take you to a file on Google Docs, Dropbox, or some other platform. On the contrary, it might link to a malware download.
FedEx/ UPS/ USPS shipping notification
Using a fake notification about a package, this message might say something like, “We could not deliver your item. Review and print your order’s complete shipping details.” The message may provide a link or have an attached file for download, neither of which are genuine.
Bank account or credit card concerns
This is a common type of message that cybercriminals use. The fraudulent message tells you that there’s an issue with your bank account or credit card account. You may be informed of irregular activity or suspicious charges, Or the message may simply request verification of your account details. You could be directed to a fake website and asked to enter your credentials. On the other hand, the message might also have a malicious attachment.
How to spot a Phishing attack ?
- Look for inconsistencies in links, addresses and domains.
Phishing emails often have email addresses that are different than the name on the email account. They may also use domain names that appear to be slightly off in some way. Users can hover on a link to check the address before clicking – often times, links will lead to sites that have nothing to do with the purported sender’s domain. - Watch out for bad spelling and grammar an unfamiliar language.
Phishing attacks often originate in other countries – watching out for unfamiliar language or inaccurate spelling can help to identify phishing emails. - Be suspicious of demands for urgent action.
Phishing attacks often demand an urgent response and may even threaten recipients with negative consequences unless they respond immediately. - Be wary of attachments.
Be completely sure of a sender’s identity before opening any attachment, even from one that appears to be from a trusted source.
How to prevent Phishing Attacks?
- Two-factor authentication (2FA)is the most effective method for countering phishing attacks, as it adds an extra verification layer when logging in to sensitive applications. 2FA relies on users having two things: something they know, such as a password and user name, and something they have, such as their smartphones. Even when employees are compromised, 2FA prevents the use of their compromised credentials, since these alone are insufficient to gain entry.
- In addition to using 2FA, organizations should enforce strict password management policies. For example, employees should be required to frequently change their passwords and to not be allowed to reuse a password for multiple applications.
- Always treat your email password like the keys to the kingdom, because that’s what it is for spammers.
- Use a short phrase for a password (longer is better, and can be simpler) rather than just a few characters, and change it regularly.
- Never share your email passwords unless you are logging in to your email provider’s website.
- Never click on links in an email – always type the address directly into the address bar.
- Keep your desktop AV, anti-spam, etc. up to date.
As the level of attacks increase, business owners cannot simply rely on anti-firewall and anti-virus solutions to block these threats. Instead, Business Owners need to proactively start looking at ways to train employees into keeping data secure. That’s where implement strong policies, and enrolling onto a Security awareness programme comes into place. These are low cost prevention tactics, which have a high impact on protecting the business.
14 Comments
Suivre Téléphone - February 11, 2024
Lorsque vous essayez d’espionner le téléphone de quelqu’un, vous devez vous assurer que le logiciel n’est pas trouvé par eux une fois qu’il est installé.
Allen Dave - October 23, 2024
Hello, as a newbie to cryptocurrency trading, I lost a lot of money trying to navigate the market on my own, then in my search for a genuine and trusted trader/broker, i came across Trader Bernie Doran who guided and helped me retrieve my lost cryptocurrencies and I made so much profit up to the tune of $60,000. I made my first investment with $2,000 and got a ROI profit of $25,000 in less than 2 week. You can contact this expert trader Mr Bernie Doran via Gmail : [email protected] or WhatsApp + 1 424 285 0682 and be ready to share your experience, tell him I referred you
Enregistrement Binance - March 31, 2024
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
online apotheek in Brussel voor kaletra - April 1, 2024
Hey there are using WordPress for your blog platform?
I’m new to the blog world but I’m trying to get started and
create my own. Do you require any html coding expertise to make your own blog?
Any help would be really appreciated!
Pivot Security - August 29, 2024
**Comment:**
This is a crucial and timely post! As phishing tactics evolve, it’s becoming increasingly important to stay informed about new threats like the one targeting Office 365 credentials. The breakdown of BEC attacks and different phishing techniques is really helpful for understanding how cybercriminals operate today. Reinforcing security with measures like two-factor authentication, strong passwords, and employee training is essential. Thanks for highlighting these points — it’s a strong reminder that awareness and proactive steps are key to safeguarding against these ever-changing threats.
https://www.pivotsec.in/
Pivot Security - August 29, 2024
**Comment:**
This is a crucial and timely post! As phishing tactics evolve, it’s becoming increasingly important to stay informed about new threats like the one targeting Office 365 credentials. The breakdown of BEC attacks and different phishing techniques is really helpful for understanding how cybercriminals operate today. Reinforcing security with measures like two-factor authentication, strong passwords, and employee training is essential. Thanks for highlighting these points — it’s a strong reminder that awareness and proactive steps are key to safeguarding against these ever-changing threat.
https://www.pivotsec.in/
binance prihlásení - November 11, 2024
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
gratis binance-konto - December 30, 2024
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
бнанс рестраця - February 1, 2025
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
Iscriviti - April 16, 2025
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
sign up for binance - June 24, 2025
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
Créer un compte gratuit - July 1, 2025
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
binance - July 16, 2025
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
Cont Binance - July 16, 2025
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.